SOAR: A Step Towards Cybersecurity Automation and Enhancement
In today’s world, where cyber threats are constantly evolving, organizations are looking for ways to enhance their security posture and respond to these threats faster and more effectively. SOAR (Security Orchestration, Automation and Response) emerges as a novel tool to assist organizations in this endeavor.
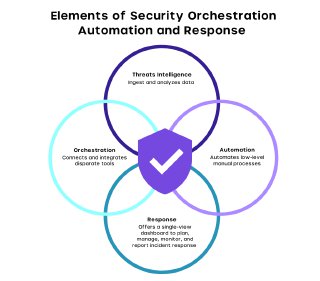
What is SOAR?
SOAR is a comprehensive platform designed to integrate, automate, and manage various security actions and tools within a single interface. By coordinating existing security systems, SOAR empowers security analysts to more effectively monitor, understand, analyze, and respond to security events.
How Does SOAR Work?
SOAR utilizes a library of pre-defined actions and customization capabilities, enabling users to automatically respond to a wide range of security events. These actions may include :
◽ Gathering information from various security sources
◽ Analyzing information to identify threats
◽ Prioritizing events based on their severity
◽ Alerting security analysts
◽ Taking actions such as blocking IPs, quarantining infected devices, and more
◽ Generating reports on security events
What are the Use Cases of SOAR?
SOAR is applicable across a broad spectrum of security use cases, including :
◽ Incident Response : SOAR can expedite and improve incident response processes by automating repetitive tasks and providing analysts with a complete view of the security posture.
◽ Threat Management : SOAR can aid in identifying and prioritizing cyber threats by gathering and analyzing information from diverse sources.
◽ Vulnerability Management : SOAR can assist organizations in keeping their systems secure by automating vulnerability scans and remediation processes.
◽ Compliance : SOAR can help organizations adhere to security regulations and standards by automating compliance processes.
What are the Goals of SOAR?
The primary objective of SOAR is to reduce the time and effort required to respond to cyber threats and overall improve the security posture of organizations. SOAR achieves this by :
◽ Automating repetitive tasks : SOAR can automate repetitive tasks like information gathering and report generation, freeing up security analysts to focus on more critical tasks.
◽ Providing a single pane of glass : SOAR can aggregate information from various security sources into a single interface, presenting analysts with a holistic view of the organization’s security posture.
◽ Enhancing decision-making : SOAR can empower security analysts to make faster and more informed decisions by providing relevant information and analysis.
SIEM vs. SOAR: What's the Difference?
SIEM (Security Information and Event Management) and SOAR are both essential security tools; however, they serve distinct purposes. SIEM focuses on collecting, storing, and analyzing security information, while SOAR concentrates on orchestrating, automating, and responding to this information. In other words, SIEM tells you what’s happening, while SOAR tells you how to respond to it.
Utilizing SIEM and SOAR in conjunction can assist organizations in establishing a comprehensive and effective security program. SIEM can provide the necessary information to SOAR for automated incident response.
What are the Key Challenges of SOAR?
◽ Implementation :
Complexity : SOAR is a complex platform that necessitates substantial technical expertise and knowledge for implementation and configuration.
Integration : SOAR must integrate with a wide range of existing security tools within the organization, which can be challenging.
Process Management : SOAR requires a robust management process to ensure its proper functioning and continuous updates.
◽ Resources :
◽ Process Change :
Adoption : SOAR may necessitate modifications to existing security processes, which could encounter resistance from employees.
◽ Maintenance :
Upkeep : SOAR demands ongoing updates and maintenance to guarantee its proper functioning and currency.
◽ Measurement Challenges :
Demonstrating ROI Value : Quantifying SOAR's effectiveness can be difficult, making it challenging to justify the return on investment (ROI).
Despite these challenges, SOAR can offer organizations significant benefits.
Conclusion
SOAR is a powerful tool that can assist organizations in enhancing their cybersecurity posture and improving their threat response capabilities. However, it is crucial to carefully consider the potential challenges and have a comprehensive plan in place to address them before implementing SOAR.